Welcome To MBEUBEU C2 Docs

👤 Whoami
I'm Insa Mane, also known as P4p4 M4n3. I'm from Senegal, i'm an electrical engineer and a security researcher .
I'm simply "A White Adversary Behind the Keyboard".
I enjoy experimenting with electronics, IoT gadgets, and other little technical gems.
👉 Donate via UNICEF
🔗 Connect with me:
• LinkedIn
• Twitter
• GitHub
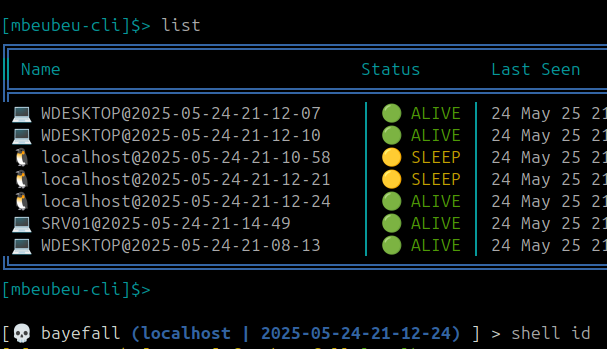
MBEUBEU is a flexible and stealthy open-source Command and Control (C2) framework designed for modern red team operations and adversary simulation. It supports multiple agent types, including Windows and Linux, and integrates advanced features for post-exploitation, evasion, and operator collaboration.
MBEUBEU is fully written in Go (Golang), making it cross-platform. The project is open to contributions from anyone who wants to help make it more powerful and adaptable.
While MBEUBEU is not yet feature-complete and doesn't aim to compete directly with other C2 frameworks, it is continuously evolving over time with community input and real-world red teaming needs in mind.
🧠 Features
- 💻 Multi-platform agent support (Windows, Linux).
- 🔐 C2 Communication fully encrypted
- 🌍 HTTP/HTTPS/QUIC listener support
- 📦 Malleable C2 profiles via YAML
- 🛡️ AV/EDR evasion, sandbox detection, smart delay
- 🛡️ Defense Analysis
- 🐚 Shell, PowerShell, and AMSI/ETW bypass execution
- 🌀 Powershell Import (pwsh-import, pwsh-execute) To import and execute .ps1
- 📷 screenshots
- 📷 Smart stealth screenshots based on window titles
- 📁 File transfer, download/upload, directory navigation
- 🎯 Lateral movement: WinRM, PSExec, PTH, DCSync
- 🪟 Credential extraction: Mimikatz, Sharpkatz, hashdump
- 🗂️ Persistence via Startup folder
- 📝 Persistence via Registry Run key
- 🔄 Persistence via Winlogon key
- ⏰ Persistence via Scheduled Task
- 🧠 In-memory BOF execution
- 🧠 In-memory .NET execute-assembly
- 📚 PowerSploit: PowerView/Mimikatz support
- 🔌 USB propagation, Office document macro injection
- 🧅 SOCKS5 proxy tunneling
- 🚨 Real-time Blue Team detection and redirection
- 📊 Reporting module: report_start / report_stop